Stop Flirting With Disaster
Is your business prepared for a disaster?
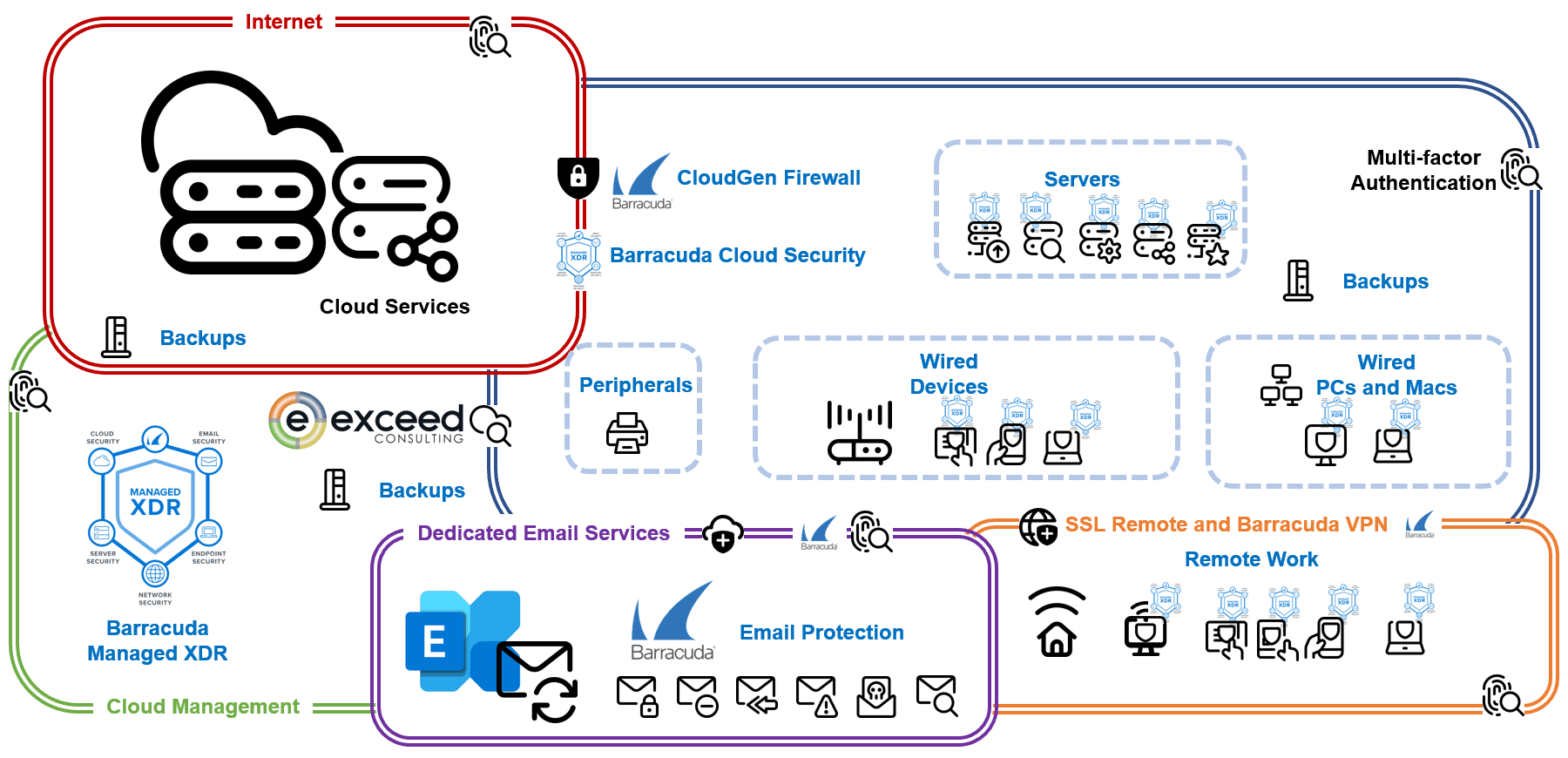
Exceed Consulting is here to help your business truly prepare for a disaster. We equip your company with the tools to safeguard against catastrophic data loss. We help you cover everything from on-premise servers and desktops to mobile devices and cloud services, ensuring you have strong protection and a robust Disaster Recovery Plan.

Reduce yout blast radius.
- Open access remediation
- Zero Trust data security
- Data access governance
Detect & stop threats.
- Ransomware
- Advanced Persistent Threat (APT)
- Insider threats
Streamline compliance.
- Data classification
- Privacy regulation auditing
- Automated Data Subject Access Requests (DSAR)
Small and mid-sized businesses are particularly vulnerable to data loss, with incidents occurring all too frequently. A hard drive failure or an overlooked backup can lead to devastating consequences. According to the U.S. National Cyber Security Alliance, 60 percent of small companies cannot sustain their businesses for over six months after a cyber-attack. With Exceed's automatic online backup and targeted recovery services, you can avoid becoming another statistic.
"The U.S. National Cyber Security Alliance found that 60 percent of small companies are unable to sustain their businesses over six months after a cyber-attack."
Our comprehensive data protection solutions include Barracuda Total Email Protection, Barracuda XDR, SentinelOne, Veeam, Storagecraft, and Synology, which are explicitly tailored to your needs. We prioritize reducing downtime with email service protection and mailbox backups, ensuring consistent access even during crises. We reinforce your defenses by employing a layered security approach with advanced threat detection and next-generation firewalls.
- Business continuity design
- Disaster recovery planning
- Secure remote backup
- Perimeter security
- Email protection and archiving
- Hardware and software monitoring
- Restore business services quickly
Proactive measures are vital in the fight against evolving cyber threats, especially ransomware attacks targeting vulnerable organizations. Simply relying on traditional firewalls and antivirus software is no longer enough. Our integrated security model incorporates Endpoint Detection & Response (EDR), actively detecting and mitigating ransomware attempts before they inflict severe damage.
- Windows Server (2000 and newer)
- Windows desktops (XP and newer)
- Linux (Red Hat, CentOS, Suse, and Ubuntu)
- Virtual machines (VMware, Hyper-V, and several others)
- Physical servers and desktops
A ransomware attack can stop your business in its tracks, often demanding exorbitant ransoms for data recovery. The best defenses rely on implementing an automated backup system and active security measures to provide seamless data protection and restoration. Implementing EDR solutions helps identify threats and maintain compliance with cyber insurance requirements.
Is Your Security Changing Fast Enough?
Given the rising cyber threats in Michigan, now is the time to reassess your security posture. Attacks have recently targeted an increasing number of prominent businesses. These attacks often reveal vulnerabilities even in seemingly secure networks. Attackers can infiltrate via unpatched systems or compromised workstations, leading to devastating data breaches.
Designing your disaster recovery plan according to your recovery goals, from minor mistakes to catastrophes, requires:
- Clear definition of tasks
- Implementation of controls and secure access
- Up to date software and hardware licensing
- Regular maintenance and patch management
- Setting realistic goals and expectations
- Setting practical recovery paths for your systems
- Understanding the bearing your design has on operations
- Regular testing of the parts, as well as the whole
Exceed Consulting engages with your team for a thorough security review to provide insights into your current vulnerabilities and recommend best practices to fortify your defenses. Our review covers corporate infrastructure assessments, intrusion protection strategies, and evaluating your ransomware response plan.
Please don't wait until it's too late. Contact Exceed today to enhance your security measures and ensure business continuity. Our expert support protects your valuable data and business operations against cyber threats.